GridHive Technology
Contents
- Introduction
- GridHive Networking and Protocols
- Nodes
- GridHive Applications
- GridHive Infrastructure
- GridHive vs the WWW
Introduction
1.1 GridHive – The Hive of Grids
GridHive (GH) is an information system with an architecture consisting of a group of loosely-coupled nodes, each owned and controlled by separate organizations or entities, which collaborate together in a highly scalable and fault-tolerant manner to exchange data or perform other tasks. Unlike traditional computing systems, GH is designed for distributed and decentralized computing, making it highly adaptable and versatile. While it is capable of performing complex tasks and calculations, its primary focus is on enabling collaboration and efficient use of resources among multiple organizations or entities.
By providing a platform for distributed computing and collaboration, GH represents a powerful tool for any organization looking to leverage the benefits of distributed computing and collaboration. Fig.1 illustrates nodes in a GridHive cluster.
The GridHive node is responsible for hosting the GH infrastructure on physical hardware, organizing the network, and performing distributed and decentralized collaboration and other computing tasks. Refer to 5.1 GridHive Node for more information on the GH Node.
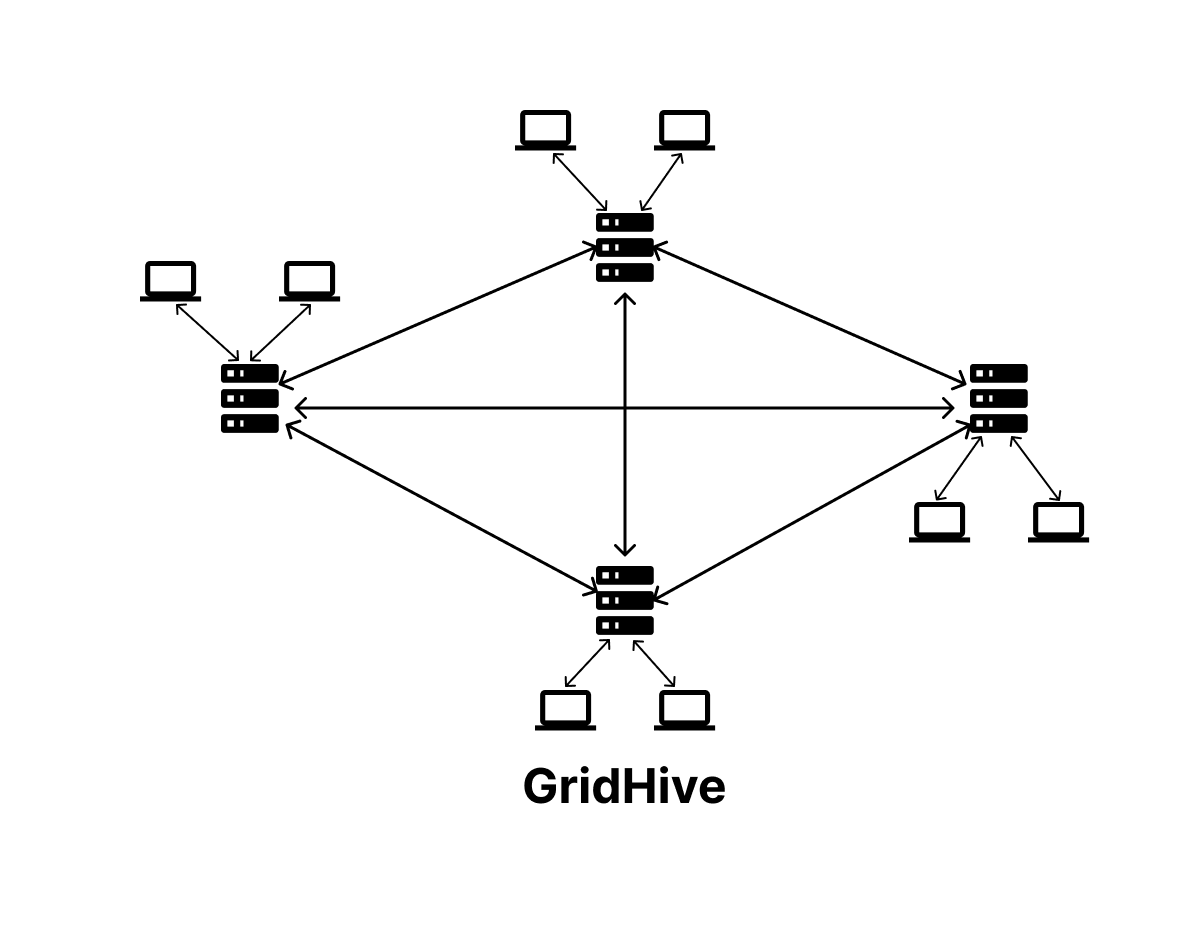
Fig.1 GridHive Architecture
"Hiving" is the connecting of two or more nodes (which may be at different geographical locations) on the GH.
Nodes can dynamically form groups, allowing organizations to share resources and collaborate while maintaining control over their individual nodes and resources.
The GH infrastructure is comprised of various unique components, they include:
- Computers: The individual computers in the GH are called nodes. Each node is responsible for hosting the GH infrastructure and the implementation and distribution of the GH technology.
- Network: The nodes in the GH are connected over a network, which allows data and processing to be transmitted between the nodes. The network must be reliable and have a sufficient bandwidth to support the communication between the nodes.
- GH management software (GH OS): The GH management software is responsible for collaboration between nodes, allocating tasks to the nodes, monitoring the progress of the tasks, and ensuring the reliable transfer of data between the nodes.
- User interface: A user interface is typically provided to allow users to access the GH technology to collaborate and perform other tasks.
1.2 Use cases of GridHive
- Energy and Engineering (EE): The EE enterprise have specific data they want to share in the GH where they are sure of privacy and security. Collaboration is important to the EE industry to enable them tackle large-scale projects.
- Pharmaceutical/Health: The pharmaceutical/health related organization may have solutions to health challenges that they may want to share with specific organizations like partners, stakeholders etc. GH makes collaboration between these organizations seamless.
- Education: GH is useful for institutions like educational or research institutions that want to be on a private network, share data with similar organizations and disseminate information. This is a useful tool for organisations or researchers of specific field to form a network and share information.
2. GridHive Protocols
GH uses a special protocol to execute its operations. Unique components of the GH networking protocol includes; users, apps, groups, and network. There are components in the GH that ensure security and privacy connection in the GH. GH uses peer-to-peer (P2P) connection.
2.1 Endonet
Endonet refers to a GH node that operates in isolation, without any external connection to other nodes. In contrast, when two or more nodes are connected, an Exonet connection is formed. Every participant in the GH is a node that can connect to other nodes when permission is granted and can exit the group at any time. The image below (Fig. 2.1) illustrates a typical GH node.
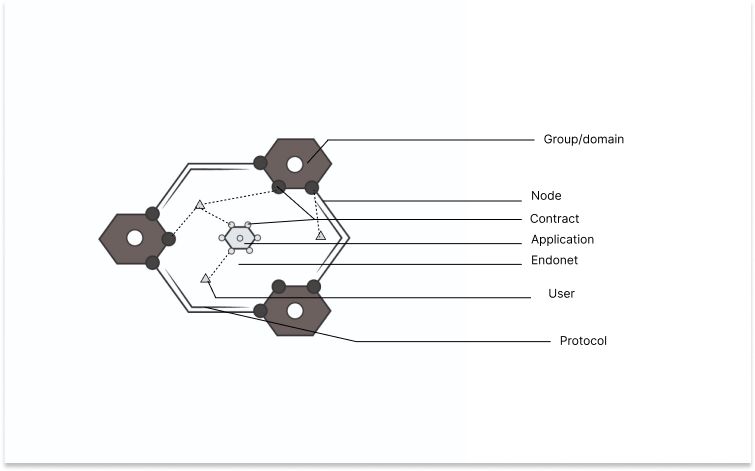
Fig.2.1 A Single Unit GridHive Node (Labelled)
In the GH infrastructure, a single unit node operates at the endonet level, without any connection to other nodes. As depicted in Fig.2.1 above, the endonet is an internal domain that allows various activities to occur within a node independently.
Users of the application within a node are considered endonet users, as shown in the same figure. To ensure privacy and security on the GH, all users are bound by groups and contracts. A contract grants a user permission to join a group, while a group provides access to applications. These measures ensure that users can only access authorized applications and data.
2.2 Exonet
Exonet refers to the external connection (node-to-node connection) within the GH. Two or more organizations in different geographical locations can connect to collaborate within a GH. Their nodes connect to each other P2P and collaboration takes place.
The following are important information about GH as related in Fig.2.2
-
The docking point between two nodes is guided by contract. If two nodes are to collaborate, the contract must be passed. This contract gives the nodes or access to the group where data can be shared and applications can be accessed.
-
Contract permission between the the nodes cannot be bypassed. It is the security of the GH and connections between the nodes is verified by the contract.
-
Data is stored inside every node. Data stored in a node stays there, cannot be accessed by another node except permission is given to it. The lock in the image (Fig.2.2) illustrates security of every node in the GH.
-
Multiple docking points between nodes are secure. Being part of the GH means the node has been given permission to to join a GridHive as seen in Fig.2.2 below
-
Sign up/password is eliminated by the architecture by contract. The nature of contract discourages connection with unfamiliar networks.
Fig. 2.2 GridHive (Multiple nodes interconnect - Exonet)
3. Node
Nodes connect on the GH for collaboration, data processing and storage. A node comprises of domains, applications, users and contracts. As shown in Fig. 2.1 above the node represents a computer. (Refer to Fig. 2.1 for more details).
All data transaction takes place in the node, and it also ensures the security of the network. A node as illustrated in the image Fig. 2.1 above is an endonet - internal data connection.
The single unit GH node illustrated in Fig. 2.1 above is a node and it comprises of domains, applications, users and contracts. This can be likened to the digital version of an enterprise operating on its own i.e no external connection.
4. GridHive Applications
Applications on the GridHive are decentralized and distributed. They follow the same principles of GridHive privacy and security.
5. GridHive Infrastructure
There are several features that make up the GH infrastructure, they are:
5.1 GridHive Node

Fig. 5.1 GH Node
The illustration in Fig. 5.1 depicts a node in the GH information system. The node is a hardware component (a computer) that performs the following functions:
- Hosts the GH infrastructure, including the GH OS and GH applications.
- Stores and backs up data.
- Shares computing resources with other nodes in the network.
- Secures the network by implementing necessary security measures.
Other enterprises in the network also have nodes that they use to access the GH and connect in a P2P fashion. It is essential to note that there are no central servers in the GH, as it is a distributed computing platform that relies on the collaboration of multiple nodes.
5.2 GridHive OS
GH OS is a GH management software that serves as the middleware for the GH, facilitating secure and collaborative distributed computing. It provides robust privacy and security features, and enables P2P access to nodes within the GH. As the operating system for the GH, it coordinates distributed and decentralized computing tasks and streamlines communication between interconnected devices ensuring collaboration within the GH.
5.3 Endonet Domain

Fig.5.3 Endonet Domain
An Endonet Domain is a virtual workspace within a single GH node where users can access applications and exchange data. It includes users, applications, and contracts, and all data transactions occur within the same node, without any external connections to other nodes.
Access to Endonet Domains is only granted through contracts, which specify the terms of the collaboration and provide permission for users to join specific groups and access particular applications. In contrast, when two or more nodes connect, a new Exonet Domain is formed, allowing external connections and collaboration between multiple nodes.
In summary, the Endonet Domain is a self-contained workspace within a single node, while the Exonet Domain enables collaboration and data exchange between multiple nodes in the GH. The illustration (Fig. 5.3) shows an endonet domain.
Fig. 5.3 represents an endonet domain, applications and contracts make up the domain. The contracts are the small circles around the hexagon while the app is represented by the small circle at the center of the hexagon.
5.4 Exonet Domain
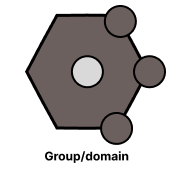
Fig. 5.4 Exonet Domain
Within the GH, domains (groups) are created to divide the network into independent partitions that operate with specific users, applications, and contracts. Domains enable collaboration between users with authorized applications. There are two types of domains in GH: internal and external. An internal domain, also known as an Endonet Domain, has no external connection. When two or more organizations collaborate and connect their respective nodes, they form an Exonet Domain. It is important to note that domains do not operate on the GH in the same way as the web; there are no domain names or identifiers.
Domains on the GH is made up of contracts and applications. The image (Fig. 5.4) shows three circles on the hexagon (representing the contracts), they connect to other nodes in the GH to give them access to applications which is represented by the small circle at the center of the hexagon.
5.5 Applications

Fig. 5.5 Application
The image (Fig. 5.5) shows an application, it is represented by the small circle at the center of the hexagon.
The availability of applications in the GH Node is strictly regulated by contracts, as shown in Fig. 2.1. The small circle in the center of the hexagon represents the application, while the six circles around it represent the contracts (Fig. 5.4).
Access to applications in any domain is only granted through permission (contract) which ensures the privacy and security of data in the GH. Therefore, users must be authorized with the necessary contracts before they can access applications in any domain.
5.6 Contract

Fig. 5.6 Contract
The GH offers a unique security mechanism, where users are required to have contracts to access any domain or collaborate with others. Without a contract, collaboration is not possible (Fig. 5.5). With this kind of security, logging in is not necessary to any domain. As long as a user is given a contract to join a domain or use an application, they have been authenticated.
With a contract in place, users are granted full access and are able to collaborate with others while being assured that both their actions and data are subject to contract rules (see Fig. 2.1).
As shown in the image above (Fig. 5.6) contract is represented by six small circles around the hexagon.
5.7 User

Fig. 5.7 User
Users on the GH network are bound by contracts when accessing domains (Fig. 2.1). Contracts specify the terms, limitations, and control within the domain and must be accepted by users before they can access domains. It is important to note that users must be granted a contract to join a domain and use applications on the GH (Fig. 5.6).
There are two types of users on the GH: endonet and exonet users. Endonet users are part of an internal domain where all data transactions happen within a node, and there are no connections to other nodes. Exonet users, on the other hand, are part of an external domain formed when two or more nodes connect.
By abiding by the rules of the contract, users are able to access domains and collaborate with others while being assured that their actions and data are subject to contract rules.
5.8 Protocol
Fig. 5.8 Protocol
The GH protocol is a unique protocol that governs the communication between nodes, grants contracts to users, and manages data control, secure data transactions, and controls connections and permissions in the network.
Protocol acts as the backbone of the network, ensuring that data transfers are secure and contracts are only granted to authorized users.
The image (Fig. 5.8) shows the GH protocol, the lock symbol shows that it is secure.
6. GridHive VS Web
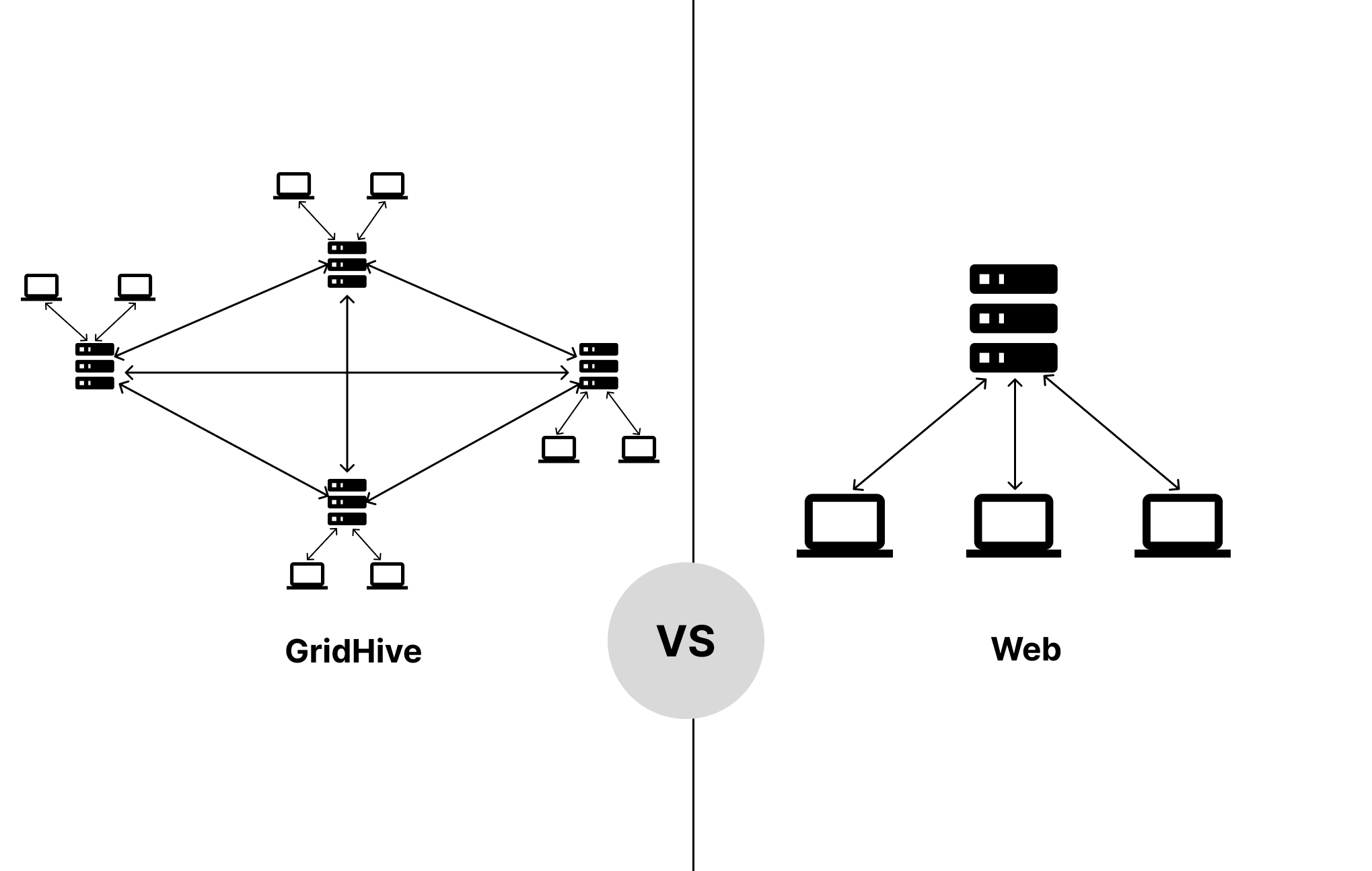
Fig. 6.1 GridHive VS Web The image (Fig. 6.1) illustrates communication within the GH and that of the web.
Here are the key differences between GH and the web
- While the web operates on a server-client model, GH is based on a node-to-node model, with communication taking place P2P.
- Applications on GH have instances on every node, while on the web, there is usually just one instance of applications that clients access via a URL.
- On GH, each node can function without connection with other nodes; on the web clients cannot function without servers.
- GH is a decentralized system, data resides with the owner of the node while on the web data typically resides with the vendor or service providers.
- GH does not depend on DNS while the web depends on DNS
GH and the web are different technologies with different purposes, but both play important roles in the distribution and access of information and computing resources over a network.
7. GridHive VS Grid Computing
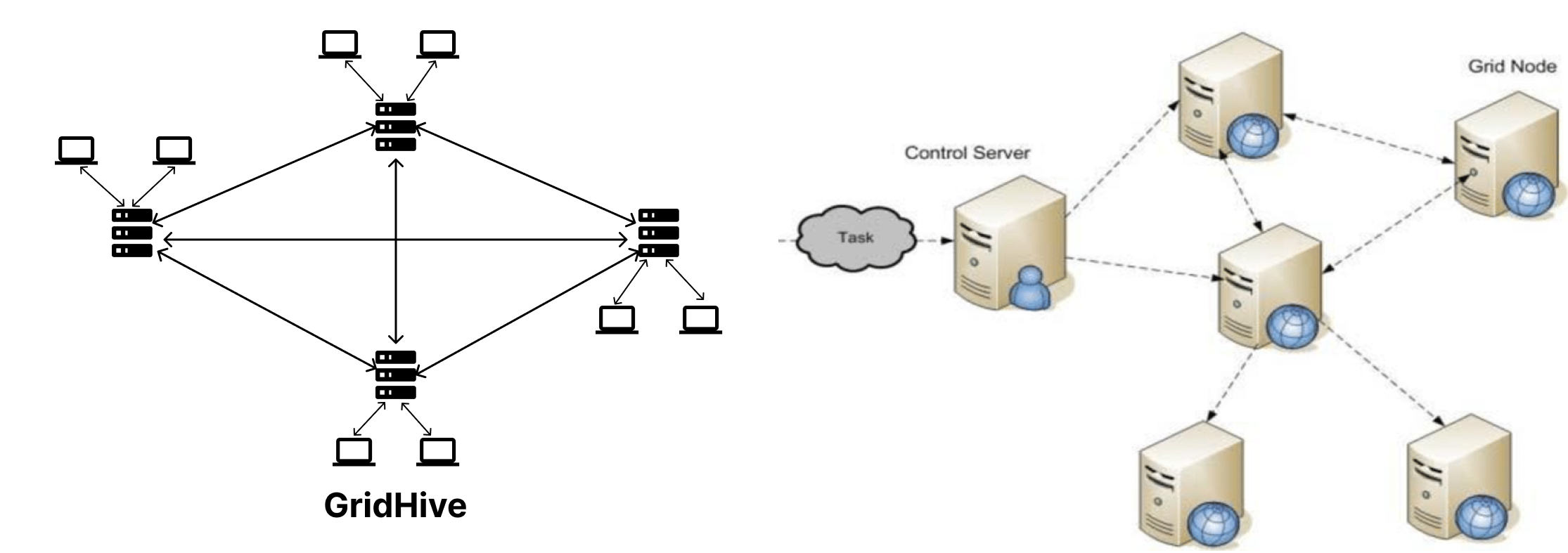
Fig.7.1 GridHive VS Grid Computing
The illustration above (Fig. 7.1) shows how connection happens on the GH and the grid computing. Notice that there are no central servers in the GH.
Grid computing aims to leverage the collective processing power of multiple computers interconnected by a network to solve intricate problems, distribute computing resources and handle computationally intensive tasks that cannot be managed by a single computer.
GH is a robust information system that enables the implementation of Grid computing with ease. GH provides a range of specialized tools, including the GH OS, to facilitate the coordination of the grid, nodes, which function as individual computers, and groups, which enhance collaborative efforts.
With GH, the potential of Grid computing can be fully realized, making it an indispensable tool for tackling complex computational problems.
8. Grid Computing VS Cloud Computing
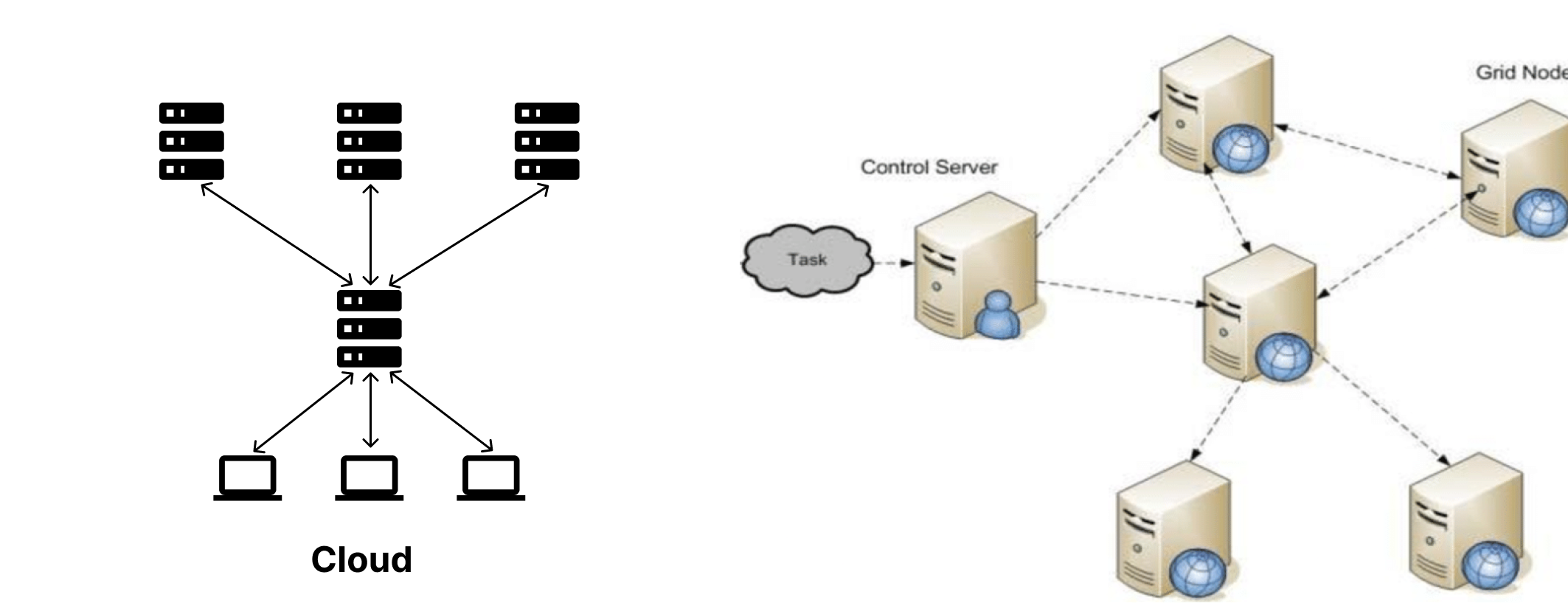
Fig.8.1 Grid Computing VS Cloud Computing
The Image above (Fig.8.1) shows grid computing networking and that of the cloud computing.
Grid computing and cloud computing are two types of distributed computing models that allow multiple users to access computing resources from multiple remote locations. However, they differ in several aspects, including:
-
Definition: Grid computing is a computing model that involves sharing computing resources across different administrative domains, while cloud computing refers to the delivery of on-demand computing resources over the internet.
-
Resource Management: Grid computing is designed to manage large amounts of data and processing power across a network of interconnected computers. In contrast, cloud computing is primarily designed for resource virtualization and allocation, enabling users to access computing resources such as processing power, storage, and applications.
-
Ownership: In grid computing, the computing resources are typically owned and managed by different organizations or individuals, and each contributor retains ownership of its own resources. On the other hand, in cloud computing, the computing resources are owned and managed by a cloud service provider, and users do not own the underlying hardware or software. Therefore, ownership of computing resources is distributed in grid computing, while it is centralized with the cloud service provider in cloud computing.
-
Use Cases: Grid computing is primarily used for scientific research, data analysis, and simulations, where large amounts of computing resources are required. Cloud computing, on the other hand, is used for a wide range of applications, including web hosting, software development, and data storage and backup.
Grid computing and cloud computing differ in their approach to resource management, infrastructure, cost, and use cases. While grid computing is designed to manage large amounts of data and processing power across multiple locations, cloud computing focuses on resource virtualization and allocation, enabling users to access computing resources on demand.